
The No Bullshit Guide to Securing WordPress
Table of Contents
So you want to stop messing around and secure your WordPress installation, eh? Well, read on. If you need help, just reach out (you can use the chat button).
Securing a website (or web server) with WordPress installations is not a simple task, and there is no one-size-fits-all solution for every installation. If you have a private blog with only you as the administrator, you can lock down your site much tighter than an ecommerce store or membership site.
Reduce your attack surface
This is the very first thing you should do. Uninstall or disable ALL functions that are not absolutely necessary. If it isn’t installed or enabled, it can’t be hacked.
If you follow the CVE Program, you will know that thousands of new vulnerabilities are discovered every day for virtually every piece of software there is. The best you can do to reduce the number of vulnerabilities you are exposed to, is to use as little software and features as possible. I cannot stress this enough.
What should you disable?
- Any plugins that are not absolutely necessary. In many cases, you can get the functionality you want using code snippets instead of installing plugins. If you do install a plugin, make sure it’s coded well and updated frequently. A good way to check the quality of your plugins is using WP Hive.
- Disable the XML-RPC endpoint (if you’re not it). This is mostly outdated and has been replaced by the newer REST API. Very few applications have a need for this. You can disable this by a plugin, code snippet or by blocking the endpoint (/xmlrpc.php) in your firewall.
- Disable the WordPress REST API for logged-out users (unless you need it). Some plugins, such as payment gateways, need access to the API. If you have a need for this, you can limit access to the endpoint to only those services, and not everyone on the internet. The REST API is best disabled or limited using a plugin or code snippet, but you can also block the endpoint (/wp-json) in your firewall. Be sure to allow if for your logged-in users, though.
- Disable WordPress User Enumeration. You can do this with a plugin, code snippet, or by blocking the end points in your firewall. If you don’t need author archives, disable them. The endpoints you need to block to avoid user enumeration are:
- /?author=
- /?author_name=
- /wp-json/wp/v2/users
- /?rest_route=/wp/v2/users
If you want to know what I use to disable unneeded features of WordPress, it’s the Perfmatters plugin. Disabling features that could compromise your installation is literally as easy as ticking a box. You can see some of the things that can be turned off below.
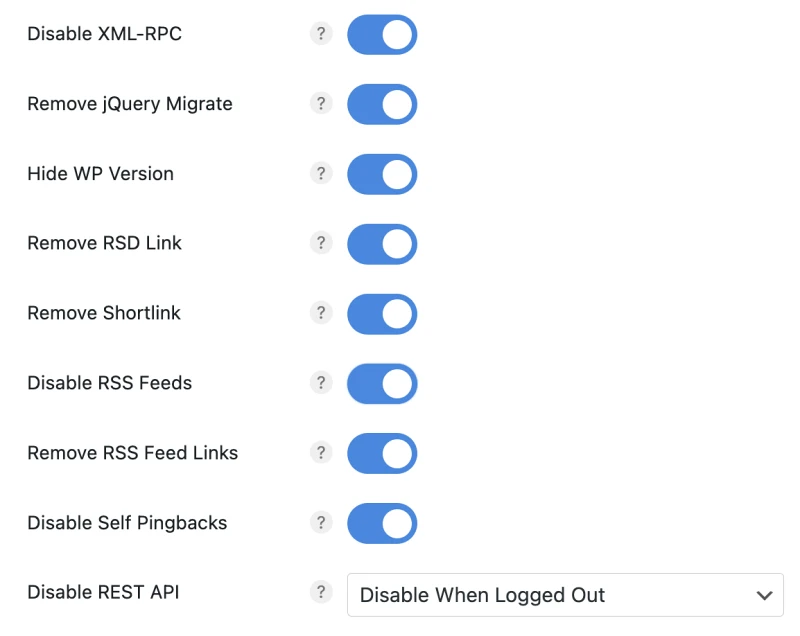
One extra advantage of turning off unnecessary features is that your instance of WordPress will run smoother and faster. This is a big part of what I do when I speed-optimize websites.
Reduce access to services
This is the second thing you do after you have figured out what services you cannot live without. An example is the WP admin dashboard (wp-admin.php). You need access to as an admin to manage your site, but you do not need to allow everyone in the world access to it.
If your internet service comes with a fixed IP, then only allow access to the admin dashboard from this IP. If you don’t have a fixed IP, there are other options such as Cloudflare Zero Trust.
In case you need your clients or customers to be able to create accounts, you will need more fine-tuned security to keep the backend safe. Some options are using Cloudflare to challenge access to wp-admin.php and wp-login.php or, if you don’t wish to use Cloudflare, you can use CrowdSec or Fail2ban. If you do not have access to the server, you can instead use a plugin to limit login attempts.
Block unnecessary access with a firewall
Make sure your firewall setup is as strict as possible, using the principle of least privilege. Only backend users (administrator, editor, etc.) need access to the dashboard. And only good bots and legitimate users need access to the frontend.
- Block bots that steal your data, bandwidth and CPU.
- Block or challenge networks (ASNs) that host the bad bots.
- Block access to PHP files to anyone except the backend users. Frontend users do not need access to any PHP files (except wp-comments.php if you allow comments on posts).
- Challenge access to PHP files from all other users with Cloudflare.
Use several layers of security
Don’t rely on only one layer of security, but use several. On my installations I use at least 3 layers: 1) Cloudflare Web Application Firewall, 2) CrowdSec, 3) a WP firewall plugin.
Use HTTPS encryption
This is another no-brainer. If you’re not using HTTPS on your website, you are seriously behind the times. You will lose the trust of your customers and also get demoted in your search engine rankings.
Make sure your web server only accepts TLS version 1.3 and above, as earlier versions are unsafe and deprecated. If you’re using Cloudflare, this is very easy to do.
Install HTTP security headers
This is usually done on the web server, but can also be done using some plugins or a code snippet. The HTTP security headers you need are:
- Strict-Transport-Security
- X-Content-Type-Options
- X-Frame-Options
- Referrer-Policy
- Content-Security-Policy
- Permissions-Policy
You can check your HTTP security headers here.
Review your user accounts
Start with removing any users that do not need access. For the remaining users, assign each user the least privilege possible that they need to do their jobs. Below is a list of WordPress user roles and capabilities:
- Super Admin – somebody with access to the site network administration features and all other features.
- Administrator (slug: ‘administrator’) – somebody who has access to all the administration features within a single site.
- Editor (slug: ‘editor’) – somebody who can publish and manage posts, including the posts of other users.
- Author (slug: ‘author’) – somebody who can publish and manage their own posts.
- Contributor (slug: ‘contributor’) – somebody who can write and manage their own posts but cannot publish them.
- Subscriber (slug: ‘subscriber’) – somebody who can only manage their profile.
Update to the latest version
This is the same principle as your personal computer and phone. Keeping the software up to date will protect you from any known vulnerabilities that have already been discovered and patched in the wild.
It will NOT protect you from zero-day vulnerabilities, so this is not sufficient on its own to ensure security of your website.
Keeping software up to date includes the WordPress core files, themes, plugins, and the version of PHP you’re using. I recommend you only use PHP version 8.1 or higher.
Do regular malware scans
If you’re managing your own VPS, you can do automatic malware scans on your server. If you’re using shared hosting, you can install a malware scanner plugin.
Take backups
Come on, guys, I don’t need to tell you this, right? You’re already taking backups, right? Seriously, you need to do backups if you’re not already, and local backups aren’t enough.
What happens if your server goes down? Or is compromised by malware? Your entire server can be infected or unreachable, in which case your local backups are useless.
That’s why you need remote backups. Keep a backlog of at least 4 weeks worth.
If you don’t have time for this
I can understand if you don’t have time for this. In that case, sign up for one of my WordPress site protection plans, and I’ll keep your website safe for you.
